Hack du RM-PRO
Pour ceux qui ne connaissent pas, le Broadlink RM-PRO est un petit boîtier dans le 40€
qui permet de piloter par WIFI depuis un smartphone (avec le prog qui va bien e-Control) toutes
vos interfaces Infra-Rouges ou RF 433MHz. Donc la TV, HIFI, prises, lumiéres RF 433Mhz.
Chouette on se dit que cela pourrait devenir votre interface entre une box domo et vos modules.
Donc recherche d'une API …
Quelques nombreuses heures plus tard, on se rend compte qu'aucune API existe, et pas de hack non plus.
Par contre quelques fous furieux ont développé une interface android qui réplique une commande UDP vers le RM.
Voici la page qui en parle :
http://milillicuti.com/rm-bridge-une-api-pour-la-passerelle-irrf-wifi-broadlink-rm-pro/
Hack perso
Bon histoire tout de même de voir ce qui en est.
Un petit coup de wireshark pour voir ce qui se passe entre un smartphone et le RM-Pro.
Au début j'ai utilisé wireshark depuis mon portable et j'ai scanné l'interface hifi (wlan)
Mais j'ai trouvé une appli sur android (shark native) qui permet de voir plus de chose.
Par contre j'utilise wireshark du portable après avoir récupérer le fichier ….pcap sur le smartphone.
Donc je lance Shark et e-Control et j'envoi une commande plusieurs fois de suite.
Voilà en gros ce que l'on peu récupérer :
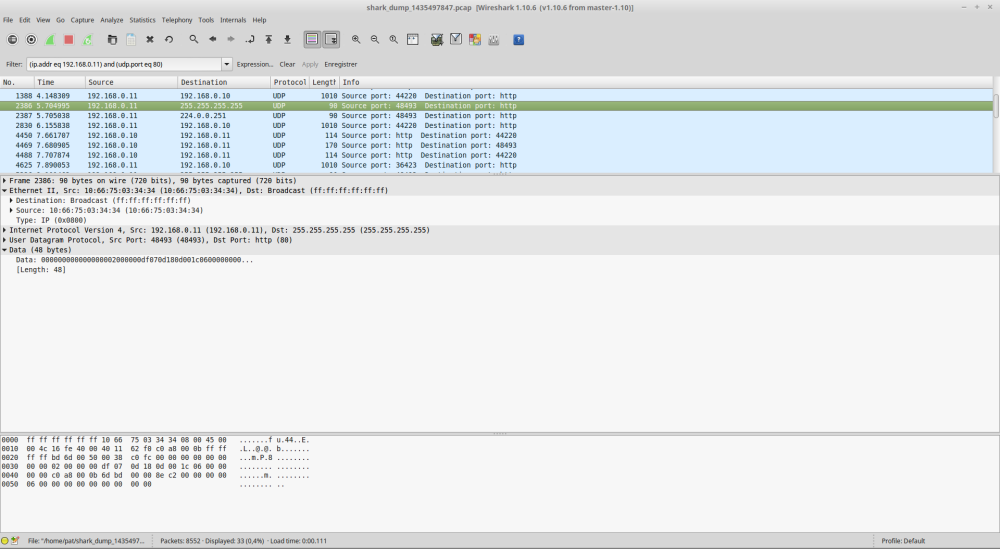
192.168.0.11 est mon smartphone
192.168.0.10 est le broadlink
Donc en gros la séquence se compose :
D'une trame UDP vers le broadcast (255.255.255.255)
data :
00:00:00:00:00:00:00:00:02:00:00:00:df:07:0d:18:0d:00:1c:06:00:00:00:00:c0:a8:00:0b:6d:bd:00:00:8e:c2:00:00:00:00:06:00:00:00:00:00:00:00:00:00
D'une trame vers un mDNS (multicast) 224.0.0.251
Cela doit être un service quelconque qui le contacte.
C'est pas important pour nous.
D'un envoi direct vers le broadlink (192.168.0.10)
data :
5a:a5:aa:55:5a:a5:aa:55:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:e0:89:00:00:12:27:6a:00:53:81:a4:0e:39:0d:43:b4:01:00:00:00:9c:10:00:00:91:68:e6:f8:30:4a:86:e8:7a:9c:33:35:f0:36:55:6b:cb:d9:80:07:7c:39:8f:88:18:2b:78:3c:a9:e9:3f:a8:57:be:ec:e4:5c:17:f4:38:bd:78:a9:a6:f5:94:28:db:47:19:50:7f:95:ca:59:81:8d:70:1e:c8:9e:38:d4:55:4a:ac:1e:61:3b:19:d7:a1:f5:7c:52:1d:2b:d7:be:5e:18:27:a3:24:63:c1:35:f8:9a:df:a2:45:8c:18:80:87:5b:21:82:13:5a:61:23:2f:5a:59:32:78:7a:1a:0f:29:6e:56:fd:62:49:2f:c7:51:a0:06:43:3d:04:2b:93:19:0a:68:d4:26:8e:d4:32:28:3d:34:6d:22:2c:da:69:e9:bd:8f:ad:1a:0b:d4:9e:58:ec:2a:33:61:61:b7:33:6b:12:64:6b:b2:ec:49:1a:f9:30:ef:56:e9:28:9b:aa:5f:d9:b3:61:01:36:03:46:be:93:cf:33:7a:d4:c5:b4:3f:17:66:f1:d7:af:c1:09:f0:0a:97:d0:40:7b:ba:f5:7e:0c:80:b8:bf:94:4a:d5:5d:2b:a0:00:fa:9b:8d:78:46:12:58:70:64:9d:e8:4c:e3:83:16:c7:dd:1b:07:a8:5b:3c:ae:5b:9b:b3:a1:ad:4f:a5:07:7a:e3:8a:25:3c:83:57:32:63:c3:f3:a2:a4:a2:d0:de:5d:a4:b6:0b:3f:b0:9f:a9:20:13:e8:d9:2d:01:05:6e:2e:cc:d1:b1:28:4c:e9:82:b1:3d:36:4b:be:0b:bb:91:72:65:79:4d:17:62:90:bc:62:c0:1d:01:d8:f4:d5:a9:b4:f7:1a:dc:1b:c3:cd:fc:bb:50:d0:05:9b:51:02:fe:2c:25:1f:64:1b:78:57:a4:03:5c:8b:09:bd:21:41:42:25:16:d6:df:b7:37:b2:c2:2e:cb:44:7a:cb:8a:b9:a0:25:82:f1:89:e4:35:82:79:7e:e6:be:4f:86:26:73:96:50:da:49:ff:50:7b:27:89:d2:5e:04:f8:5a:ee:69:02:9d:da:4e:37:bc:08:7a:cb:d8:5e:99:10:6c:e6:a2:6d:95:57:91:ed:f6:8b:0c:a1:47:b1:6f:6c:7e:77:e1:92:a1:0d:b8:a9:7b:37:1b:41:4f:d4:c8:c1:a3:f5:c5:1b:de:e3:89:30:07:7c:f6:29:78:f2:22:e0:ea:55:cc:98:5e:93:ec:13:5e:32:13:ff:f9:92:40:51:34:58:74:93:86:08:3a:45:ae:f3:bf:bc:99:ce:d3:e3:cc:25:09:44:a9:94:ce:72:c1:bc:a1:41:d0:7e:7c:90:32:f7:20:a0:f3:a7:38:ea:a2:3b:1c:0b:f8:0a:7e:83:81:80:5e:72:44:2d:a1:77:b4:7c:9c:c0:ec:03:c7:b7:2d:f5:0c:0b:e1:ca:b2:55:d1:16:5f:70:e6:30:d9:65:00:bf:ce:7c:c7:4e:41:51:df:98:75:90:c0:ce:44:90:dd:ce:a9:07:ac:f2:1c:44:27:a6:b5:76:3f:90:d4:97:4a:c7:9b:b5:f0:40:b1:f4:29:74:8d:ca:d5:90:7f:ea:29:c5:2b:75:ce:49:81:df:75:0e:91:9a:d8:19:63:24:a1:51:0e:6b:08:22:5f:d6:ac:44:fd:6b:ac:ac:28:7c:b2:f4:03:76:ac:3b:5d:62:28:2b:73:a4:e1:d7:9c:40:9a:09:26:9c:d9:d8:d1:75:52:70:6a:68:70:fa:ff:42:23:de:82:a7:ae:c8:14:f2:a2:3d:35:f1:9e:05:3e:00:ff:b0:97:29:0f:7b:19:a9:76:1c:c7:e8:a1:58:97:5e:00:cb:59:ca:7b:85:9f:28:3f:18:7b:4b:85:a4:cb:ee:59:df:e9:3d:91:a9:57:c0:e7:0d:de:4d:04:d9:bd:fa:eb:bf:1a:19:59:9f:0c:97:ae:65:e1:75:24:d5:9c:fa:4a:85:dd:9e:12:84:b2:b6:f0:a4:6b:f3:34:18:c9:a0:99:21:97:b2:fc:b6:3f:5a:d8:ac:2d:b7:7a:47:78:4c:5b:02:db:c1:e2:5e:86:0e:c6:6f:8c:91:b6:6a:7e:c6:00:0d:62:fa:16:9c:19:26:2a:33:c5:71:b6:c7:92:6f:7e:7d:f2:04:5f:ce:c3:20:bc:80:4d:f9:01:64:32:ff:c0:11:c6:63:42:c2:65:c7:ea:cf:7f:46:89:7f:b3:3d:31:93:a3:d7:6a:12:04:ac:35:15:cd:21:9d:54:58:af:ed:32:85:8a:8d:2a:e0:ee:11:21:ed:48:5f:7b:88:7f:6a:54:81:58:f2:8c:68:79:5a:fe:12:d2:d8:cb:44:70:f9:cc:81:08:8f:47:e4:e6:b7:94:c5:e8:fc:40:27:fc:86:40:5b:1c:02:01:13:94:84:cc
Ensuite nous avons la réponse du broadlink, elle peu être en 2 ou 3 trame.
192.168.0.10 → 192.168.0.11
data
5a:a5:aa:55:5a:a5:aa:55:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:54:d0:00:00:12:27:ee:03:53:81:a4:0e:39:0d:43:b4:01:00:00:00:d8:c0:00:00:91:68:e6:f8:30:4a:86:e8:7a:9c:33:35:f0:36:55:6b
Une autre ligne :
data
00:00:00:00:00:00:00:00:02:00:00:00:df:07:0d:18:0d:00:1c:06:00:00:00:00:c0:a8:00:0b:6d:bd:00:00:0f:d1:00:00:00:00:07:00:00:00:00:00:00:00:00:00:c9:bd:b7:1e:12:27:0a:00:a8:c0:a4:0e:39:0d:43:b4:e6:99:ba:e8:83:bd:e9:81:a5:e6:8e:a7:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00
Encore une toujours du broadlink vers le smartphone.
data :
5a:a5:aa:55:5a:a5:aa:55:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:54:d0:00:00:12:27:ee:03:53:81:a4:0e:39:0d:43:b4:01:00:00:00:d8:c0:00:00:91:68:e6:f8:30:4a:86:e8:7a:9c:33:35:f0:36:55:6b
En fait les même data que la première réponse .
Et enfin un retour du smartphone vers broadlink.
data :
5a:a5:aa:55:5a:a5:aa:55:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:dd:89:00:00:12:27:6a:00:51:80:a4:0e:39:0d:43:b4:01:00:00:00:9c:10:00:00:91:68:e6:f8:30:4a:86:e8:7a:9c:33:35:f0:36:55:6b:cb:d9:80:07:7c:39:8f:88:18:2b:78:3c:a9:e9:3f:a8:57:be:ec:e4:5c:17:f4:38:bd:78:a9:a6:f5:94:28:db:47:19:50:7f:95:ca:59:81:8d:70:1e:c8:9e:38:d4:55:4a:ac:1e:61:3b:19:d7:a1:f5:7c:52:1d:2b:d7:be:5e:18:27:a3:24:63:c1:35:f8:9a:df:a2:45:8c:18:80:87:5b:21:82:13:5a:61:23:2f:5a:59:32:78:7a:1a:0f:29:6e:56:fd:62:49:2f:c7:51:a0:06:43:3d:04:2b:93:19:0a:68:d4:26:8e:d4:32:28:3d:34:6d:22:2c:da:69:e9:bd:8f:ad:1a:0b:d4:9e:58:ec:2a:33:61:61:b7:33:6b:12:64:6b:b2:ec:49:1a:f9:30:ef:56:e9:28:9b:aa:5f:d9:b3:61:01:36:03:46:be:93:cf:33:7a:d4:c5:b4:3f:17:66:f1:d7:af:c1:09:f0:0a:97:d0:40:7b:ba:f5:7e:0c:80:b8:bf:94:4a:d5:5d:2b:a0:00:fa:9b:8d:78:46:12:58:70:64:9d:e8:4c:e3:83:16:c7:dd:1b:07:a8:5b:3c:ae:5b:9b:b3:a1:ad:4f:a5:07:7a:e3:8a:25:3c:83:57:32:63:c3:f3:a2:a4:a2:d0:de:5d:a4:b6:0b:3f:b0:9f:a9:20:13:e8:d9:2d:01:05:6e:2e:cc:d1:b1:28:4c:e9:82:b1:3d:36:4b:be:0b:bb:91:72:65:79:4d:17:62:90:bc:62:c0:1d:01:d8:f4:d5:a9:b4:f7:1a:dc:1b:c3:cd:fc:bb:50:d0:05:9b:51:02:fe:2c:25:1f:64:1b:78:57:a4:03:5c:8b:09:bd:21:41:42:25:16:d6:df:b7:37:b2:c2:2e:cb:44:7a:cb:8a:b9:a0:25:82:f1:89:e4:35:82:79:7e:e6:be:4f:86:26:73:96:50:da:49:ff:50:7b:27:89:d2:5e:04:f8:5a:ee:69:02:9d:da:4e:37:bc:08:7a:cb:d8:5e:99:10:6c:e6:a2:6d:95:57:91:ed:f6:8b:0c:a1:47:b1:6f:6c:7e:77:e1:92:a1:0d:b8:a9:7b:37:1b:41:4f:d4:c8:c1:a3:f5:c5:1b:de:e3:89:30:07:7c:f6:29:78:f2:22:e0:ea:55:cc:98:5e:93:ec:13:5e:32:13:ff:f9:92:40:51:34:58:74:93:86:08:3a:45:ae:f3:bf:bc:99:ce:d3:e3:cc:25:09:44:a9:94:ce:72:c1:bc:a1:41:d0:7e:7c:90:32:f7:20:a0:f3:a7:38:ea:a2:3b:1c:0b:f8:0a:7e:83:81:80:5e:72:44:2d:a1:77:b4:7c:9c:c0:ec:03:c7:b7:2d:f5:0c:0b:e1:ca:b2:55:d1:16:5f:70:e6:30:d9:65:00:bf:ce:7c:c7:4e:41:51:df:98:75:90:c0:ce:44:90:dd:ce:a9:07:ac:f2:1c:44:27:a6:b5:76:3f:90:d4:97:4a:c7:9b:b5:f0:40:b1:f4:29:74:8d:ca:d5:90:7f:ea:29:c5:2b:75:ce:49:81:df:75:0e:91:9a:d8:19:63:24:a1:51:0e:6b:08:22:5f:d6:ac:44:fd:6b:ac:ac:28:7c:b2:f4:03:76:ac:3b:5d:62:28:2b:73:a4:e1:d7:9c:40:9a:09:26:9c:d9:d8:d1:75:52:70:6a:68:70:fa:ff:42:23:de:82:a7:ae:c8:14:f2:a2:3d:35:f1:9e:05:3e:00:ff:b0:97:29:0f:7b:19:a9:76:1c:c7:e8:a1:58:97:5e:00:cb:59:ca:7b:85:9f:28:3f:18:7b:4b:85:a4:cb:ee:59:df:e9:3d:91:a9:57:c0:e7:0d:de:4d:04:d9:bd:fa:eb:bf:1a:19:59:9f:0c:97:ae:65:e1:75:24:d5:9c:fa:4a:85:dd:9e:12:84:b2:b6:f0:a4:6b:f3:34:18:c9:a0:99:21:97:b2:fc:b6:3f:5a:d8:ac:2d:b7:7a:47:78:4c:5b:02:db:c1:e2:5e:86:0e:c6:6f:8c:91:b6:6a:7e:c6:00:0d:62:fa:16:9c:19:26:2a:33:c5:71:b6:c7:92:6f:7e:7d:f2:04:5f:ce:c3:20:bc:80:4d:f9:01:64:32:ff:c0:11:c6:63:42:c2:65:c7:ea:cf:7f:46:89:7f:b3:3d:31:93:a3:d7:6a:12:04:ac:35:15:cd:21:9d:54:58:af:ed:32:85:8a:8d:2a:e0:ee:11:21:ed:48:5f:7b:88:7f:6a:54:81:58:f2:8c:68:79:5a:fe:12:d2:d8:cb:44:70:f9:cc:81:08:8f:47:e4:e6:b7:94:c5:e8:fc:40:27:fc:86:40:5b:1c:02:01:13:94:84:cc
Donc si on regarde un peu, on a le même début que la réponse précédente jusqu'après la première suite de 00 où l'on a :
....:00:00:dd:89:00:00:12:27:6a:00:51:80:a4:0e:39:0d:43:b4:01:00:00:00:9c:10:00:00:91:68:e6:f8:30:4a:86:e8:7a:9c:33:35:f0:36:55:6b
D'ailleurs la fin ressemble aussi :
00:00:91:68:e6:f8:30:4a:86:e8:7a:9c:33:35:f0:36:55:6b
Le changement se fait ici :
retour rm → phone et 2ieme ligne phone → rm
:54:d0:00:00:12:27:ee:03:53:81:a4:0e:39:0d:43:b4:01:00:00:00:d8:c0
:dd:89:00:00:12:27:6a:00:51:80:a4:0e:39:0d:43:b4:01:00:00:00:9c:10
1iere conclusions
Le Smartphone envoi un code au broadcast pour préparer le(ou les) RM a un ordre.
Il envoi ensuite sans doute un ordre.
Le RM renvoi une sorte de ACK
Le Smartphone accuse le ACK.
On pourrait se dire super j'envoie la même séquence.
Mais non car si on annalyse les codes envoyés par la même commande.
Différents Broadcast envoyés:
00:00:00:00:00:00:00:00:02:00:00:00:df:07:0d:18:0d:00:1c:06:00:00:00:00:c0:a8:00:0b:6d:bd:00:00:8e:c2:00:00:00:00:06:00:00:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00:02:00:00:00:df:07:11:18:0d:00:1c:06:00:00:00:00:c0:a8:00:0b:6d:bd:00:00:92:c2:00:00:00:00:06:00:00:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00:02:00:00:00:df:07:14:18:0d:00:1c:06:00:00:00:00:c0:a8:00:0b:6d:bd:00:00:95:c2:00:00:00:00:06:00:00:00:00:00:00:00:00:00
On a déjà une différence sur 1 octet après 00:00:00:df:07:
0d pour le 1°
11 pour le 2°
14 pour le dernier
ça s'annonce pas cool, il ne s'agit peut être que des indications sur l'heure d'envoi.
On regarde le premier transfert entre le smartphone vers le broadlink
5a:a5:aa:55:5a:a5:aa:55:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:e0:89:00:00:12:27:6a:00:53:81:a4:0e:39:0d:43:b4:01:00:00:00:9c:10:00:00:91:68:e6:f8:30:4a:86:e8:7a:9c:33:35:f0:36:55:6b:cb:d9:80:07:7c:39:8f:88:18:2b:78:3c:a9:e9:3f:a8:57:be:ec:e4:5c:17:f4:38:bd:78:a9:a6:f5:94:28:db:47:19:50:7f:95:ca:59:81:8d:70:1e:c8:9e:38:d4:55:4a:ac:1e:61:3b:19:d7:a1:f5:7c:52:1d:2b:d7:be:5e:18:27:a3:24:63:c1:35:f8:9a:df:a2:45:8c:18:80:87:5b:21:82:13:5a:61:23:2f:5a:59:32:78:7a:1a:0f:29:6e:56:fd:62:49:2f:c7:51:a0:06:43:3d:04:2b:93:19:0a:68:d4:26:8e:d4:32:28:3d:34:6d:22:2c:da:69:e9:bd:8f:ad:1a:0b:d4:9e:58:ec:2a:33:61:61:b7:33:6b:12:64:6b:b2:ec:49:1a:f9:30:ef:56:e9:28:9b:aa:5f:d9:b3:61:01:36:03:46:be:93:cf:33:7a:d4:c5:b4:3f:17:66:f1:d7:af:c1:09:f0:0a:97:d0:40:7b:ba:f5:7e:0c:80:b8:bf:94:4a:d5:5d:2b:a0:00:fa:9b:8d:78:46:12:58:70:64:9d:e8:4c:e3:83:16:c7:dd:1b:07:a8:5b:3c:ae:5b:9b:b3:a1:ad:4f:a5:07:7a:e3:8a:25:3c:83:57:32:63:c3:f3:a2:a4:a2:d0:de:5d:a4:b6:0b:3f:b0:9f:a9:20:13:e8:d9:2d:01:05:6e:2e:cc:d1:b1:28:4c:e9:82:b1:3d:36:4b:be:0b:bb:91:72:65:79:4d:17:62:90:bc:62:c0:1d:01:d8:f4:d5:a9:b4:f7:1a:dc:1b:c3:cd:fc:bb:50:d0:05:9b:51:02:fe:2c:25:1f:64:1b:78:57:a4:03:5c:8b:09:bd:21:41:42:25:16:d6:df:b7:37:b2:c2:2e:cb:44:7a:cb:8a:b9:a0:25:82:f1:89:e4:35:82:79:7e:e6:be:4f:86:26:73:96:50:da:49:ff:50:7b:27:89:d2:5e:04:f8:5a:ee:69:02:9d:da:4e:37:bc:08:7a:cb:d8:5e:99:10:6c:e6:a2:6d:95:57:91:ed:f6:8b:0c:a1:47:b1:6f:6c:7e:77:e1:92:a1:0d:b8:a9:7b:37:1b:41:4f:d4:c8:c1:a3:f5:c5:1b:de:e3:89:30:07:7c:f6:29:78:f2:22:e0:ea:55:cc:98:5e:93:ec:13:5e:32:13:ff:f9:92:40:51:34:58:74:93:86:08:3a:45:ae:f3:bf:bc:99:ce:d3:e3:cc:25:09:44:a9:94:ce:72:c1:bc:a1:41:d0:7e:7c:90:32:f7:20:a0:f3:a7:38:ea:a2:3b:1c:0b:f8:0a:7e:83:81:80:5e:72:44:2d:a1:77:b4:7c:9c:c0:ec:03:c7:b7:2d:f5:0c:0b:e1:ca:b2:55:d1:16:5f:70:e6:30:d9:65:00:bf:ce:7c:c7:4e:41:51:df:98:75:90:c0:ce:44:90:dd:ce:a9:07:ac:f2:1c:44:27:a6:b5:76:3f:90:d4:97:4a:c7:9b:b5:f0:40:b1:f4:29:74:8d:ca:d5:90:7f:ea:29:c5:2b:75:ce:49:81:df:75:0e:91:9a:d8:19:63:24:a1:51:0e:6b:08:22:5f:d6:ac:44:fd:6b:ac:ac:28:7c:b2:f4:03:76:ac:3b:5d:62:28:2b:73:a4:e1:d7:9c:40:9a:09:26:9c:d9:d8:d1:75:52:70:6a:68:70:fa:ff:42:23:de:82:a7:ae:c8:14:f2:a2:3d:35:f1:9e:05:3e:00:ff:b0:97:29:0f:7b:19:a9:76:1c:c7:e8:a1:58:97:5e:00:cb:59:ca:7b:85:9f:28:3f:18:7b:4b:85:a4:cb:ee:59:df:e9:3d:91:a9:57:c0:e7:0d:de:4d:04:d9:bd:fa:eb:bf:1a:19:59:9f:0c:97:ae:65:e1:75:24:d5:9c:fa:4a:85:dd:9e:12:84:b2:b6:f0:a4:6b:f3:34:18:c9:a0:99:21:97:b2:fc:b6:3f:5a:d8:ac:2d:b7:7a:47:78:4c:5b:02:db:c1:e2:5e:86:0e:c6:6f:8c:91:b6:6a:7e:c6:00:0d:62:fa:16:9c:19:26:2a:33:c5:71:b6:c7:92:6f:7e:7d:f2:04:5f:ce:c3:20:bc:80:4d:f9:01:64:32:ff:c0:11:c6:63:42:c2:65:c7:ea:cf:7f:46:89:7f:b3:3d:31:93:a3:d7:6a:12:04:ac:35:15:cd:21:9d:54:58:af:ed:32:85:8a:8d:2a:e0:ee:11:21:ed:48:5f:7b:88:7f:6a:54:81:58:f2:8c:68:79:5a:fe:12:d2:d8:cb:44:70:f9:cc:81:08:8f:47:e4:e6:b7:94:c5:e8:fc:40:27:fc:86:40:5b:1c:02:01:13:94:84:cc
Bon je vous fait grâce des autres, en fait on se rends compte que seul qq octets changent aprèe la première suite de 00.
00:e0:89:00:00:12:27:6a:00:53:81
00:dd:89:00:00:12:27:6a:00:51:80
00:dc:89:00:00:12:27:6a:00:4f:81
:**: :**:**
On regarde la réponse du broadlink au smartphone.
5a:a5:aa:55:5a:a5:aa:55:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:54:d0:00:00:12:27:ee:03:53:81:a4:0e:39:0d:43:b4:01:00:00:00:d8:c0:00:00:91:68:e6:f8:30:4a:86:e8:7a:9c:33:35:f0:36:55:6b
Et pareil que pour le précédent, seul quelques octets changent après la première suite de 00.
00:54:d0:00:00:12:27:ee:03:53:81
00:51:d0:00:00:12:27:ee:03:51:80
00:50:d0:00:00:12:27:ee:03:4f:81
:**: :**:**
Et on se rend compte que ce sont les mêmes que le précédent.
Ma conclusion
En fait j'ai l'impression qu'il ne s'agit que d'une information sur l'heure qui change.
Comment c'est codé ???
J'ai essayé d'envoyer les même séquences en UDP pour voir.
La led du Broadlink s'allume, mais l'ordre n'est pas exécuté.
Bilan
Hacker la bête semble pas si facile que cela.
Au vue des fichiers de conf fourni par les liens du site cité en tête de page.
init.d2l
{
"api_id" : 1,
"command" : "network_init",
"license" :
"hXZiAvxNl65WX29d0rbNkiO6O/EoAC26K60zaushO2raU5ilXywBh7Jg6awMUV52iVlVZq7x/5elBh47qYMMwpRSYh5e4Txcrw9UfrrF7KZr5jRqWAw=",
"main_udp_ser" : "www.baidu.com",
"backup_udp_ser" : "www.sina.com.cn",
"main_tcp_ser" : "www.google.com",
"main_udp_port" : 80,
"backup_udp_port" : 8080,
"main_tcp_port" : 80
}
et choice.d2l
{ "api_id":12,
"command":"device_add",
"mac":"b4:43:0d:38:6b:c3",
"type":"RM2",
"name":"Smart Plug",
"lock":0, "password":1003837149,
"id":0,
"subdevice":0,"key":"530ce6718a7f5c61c0f2d250f7654940"
}
On voit qu'il y a une licence ainsi qu'un password.
Ceci est une première approche, je ne suis pas assez calé pour aller beaucoup plus loin.
Si certain sont intéressés voici le fichier pcap de la capture ainsi qu'un fichier épuré en txt.
shark_dump_1435497847.pcap
lampe.cap


